Plus, our consultant will introduce you to the Mental Fitness approach – our unique method designed to help you stay stress-free, resilient, and confident throughout your learning journey!
Cyber Security + AI
The course will be held in English
Lectures are live - in real time with the lecturer (+ recordings of AI e-lectures)
The course will be held remotely (online)
Duration: 100 hours, 34 days
Time: 3 times a week, 3 hours each, from 7:30 pm - 10:30 pm (UTC +2 time zone) in the evenings
Begin your cybersecurity career with our beginner-friendly course led by experienced lecturers. You’ll explore daily security threats, ethical hacking, vulnerability assessment, and networking essentials like LAN/WAN configurations and tools like Nmap and Wireshark. Gain hands-on experience in web security, cloud fundamentals, and server hardening while mastering cryptography and penetration testing. By the end, you’ll be ready to tackle real-world cybersecurity challenges and confidently apply for industry roles.
K2 College Extras
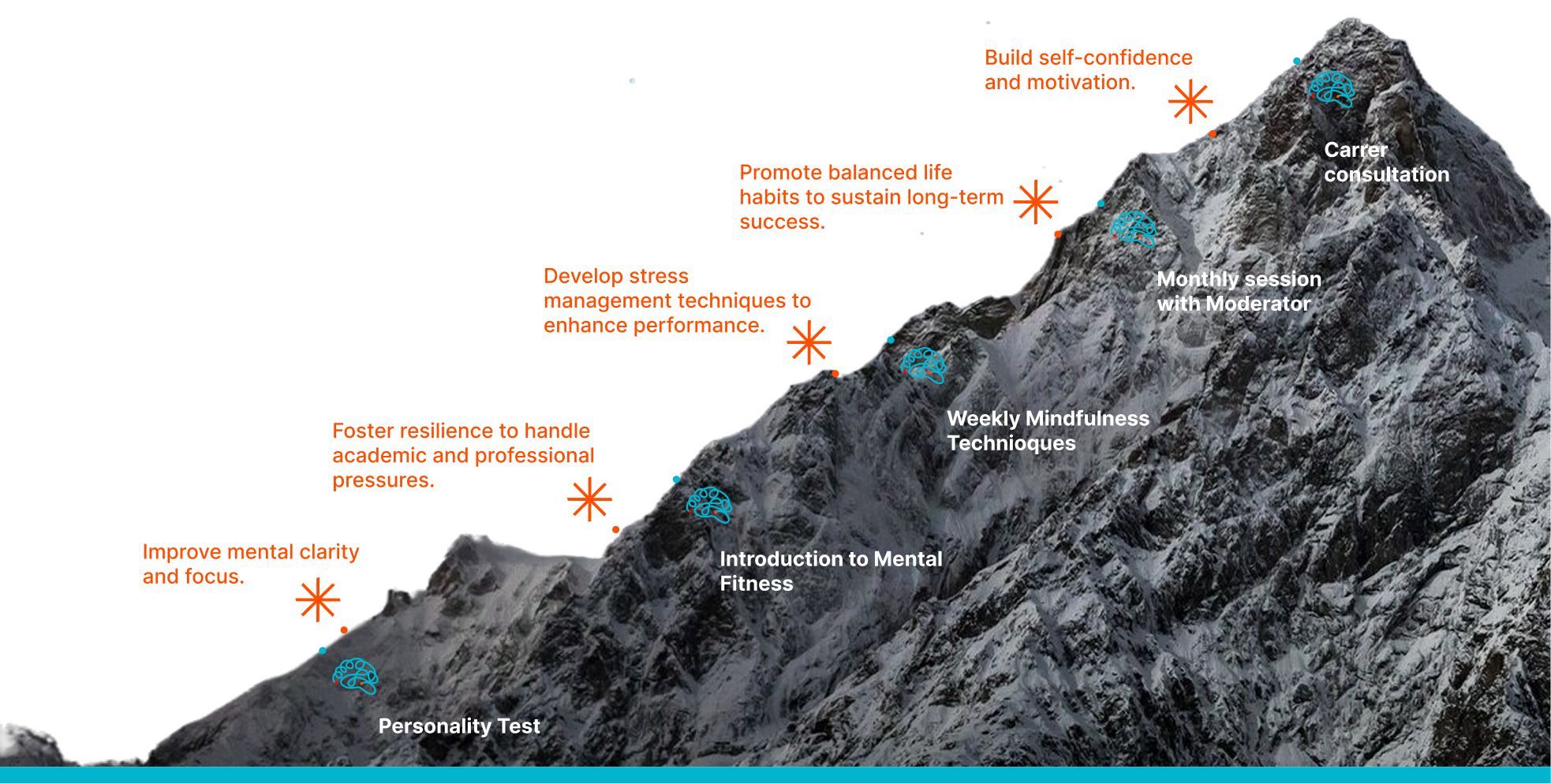
Your Journey to the Top
Download Brochure for this course
Sneak peek into the training
Not Sure Where to Begin? A Quick Consultation Will Help.
Which course could lead to your dream career? How much time should you dedicate to learning? Are you eligible for financial aid? Our Career Center consultants will give detailed answers and ask the right questions to help you choose a course that fits your career goals and matches your skills and strengths.
What you will learn
Build your cybersecurity skills with a program based on the most recent developments in the field and case studies that have formed our understanding of the internet's safety practices.
K2College is the first in the world to integrate Mental Fitness into tech bootcamps.
Learn in real time. Stay resilient. Come back to refresh anytime – once a K2 student, always part of our learning community.
Foundations of Cybersecurity
Learn essential concepts and principles in cybersecurity and understand common security threats, malware types, and defence strategies.
Operating System Security and Threat Management
Master basic command-line interface (CLI) operations for security management and learn techniques for identifying and mitigating daily security threats.
Network Security Fundamentals
Learn computer networking and network security principles and understand LAN/WAN configurations, firewalls, and network scanning tools.
Cryptography and Secure Communication
Study the basics of cryptography, including symmetric and asymmetric encryption, and apply encryption techniques for secure communication.
Security Policies, Compliance, and Risk Assessment
Learn about the vast array of security policies and compliance requirements and acquire the fundamentals of risk assessment in cybersecurity contexts.
Web Application Security
Practice identifying and mitigating common web application vulnerabilities and implement secure coding practices and techniques.
Penetration Testing and Ethical Hacking
Learn the techniques for intelligence gathering and information reconnaissance and get hands-on experience with vulnerability scanning and penetration testing tools.
Register for this course
RegisterTraditional Training vs. Mental Fitness Approach
There are many routes to a new career, and only you know which suits you the best. Explore our tried-and-true courses and pick the one you’ll conquer.
Meet our Climbers
Nothing inspires more than a success story. And here’s just a few we’ve guided over the years.
Study without burnout
The training went really well, and the lecturers left nothing but good feedback. The training provided a fundamental introduction to three tools: SQL, PowerBI and Python. I found a job within a month, maybe a month and a half.
Study without burnout
Thank you for the professional, fun, and well-organised courses. Thank you for your insight into each project, your individual approach, encouragement, and help. It is a great pleasure and satisfaction that you have invited me into the design world!
Study without burnout
Very good school with excellent, knowledgeable teachers. Keep in mind that you have spend your free time developing skills and be self-disciplined. How good a programmer you will be is up to you and your interest in programming.
Study without burnout
I've completed the Data Analytics Course. It was an intense journey where I learned SQL, Power BI, and the basics of Python. I was very satisfied with the course quality and the whole experience. My lectutrer's strong teaching skills, expertise, and patience made the learning experience truly enjoyable. Learning from a professional was an honour.
Study without burnout
I really liked the length of the training programme. It went very well, and one of the reasons why I liked the training so much was that lecturer was a very good lecturer and mentor. I increased my existing knowledge of front-end programming, and I also learned back-end technologies and database management.
Get your FREE GUIDE
Inside, you’ll find science-backed micro-habits to help you feel calmer, more focused, and emotionally stronger—one small step at a time.

Career Center
Visit our Career CenterPersonal career planning
Mandatory soft skill training
Online mental fitness resources
Lifetime access to events
Have Any Questions?
Have Any Questions?
Fill the form and our team will contact you shortly.

We Are Part of